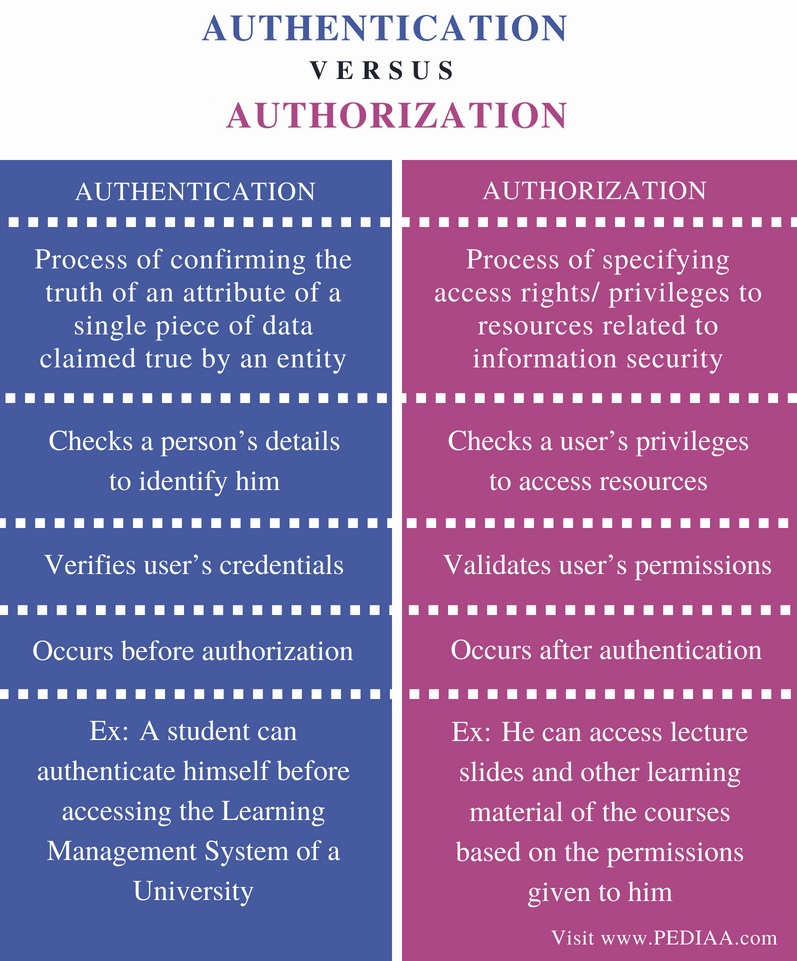
What Is Authorization And Access Control . Authentication isn’t sufficient by itself to. authentication is the first step in access control. in its simplest form, access control involves identifying a user based on their credentials and then authorizing the appropriate level. It involves verifying the identity of the user or system requesting access. authentication is a technique used to verify that someone is who they claim to be. access control enforces both authentication and authorization policies to regulate access. authentication and authorization are two vital information security processes that administrators use to protect systems and. authorization is the process of matching users to the right digital assets. The work starts with policy. Authentication verifies the identity of the user,. authentication is the process of verifying someone’s claimed identity, while authorization determines what. This is usually done by.
from www.sexiezpicz.com
authentication is the first step in access control. Authentication isn’t sufficient by itself to. The work starts with policy. Authentication verifies the identity of the user,. It involves verifying the identity of the user or system requesting access. authentication is a technique used to verify that someone is who they claim to be. in its simplest form, access control involves identifying a user based on their credentials and then authorizing the appropriate level. authorization is the process of matching users to the right digital assets. This is usually done by. access control enforces both authentication and authorization policies to regulate access.
Authentication Vs Authorization Differences And Similarities Beyond
What Is Authorization And Access Control Authentication verifies the identity of the user,. authorization is the process of matching users to the right digital assets. access control enforces both authentication and authorization policies to regulate access. authentication is the process of verifying someone’s claimed identity, while authorization determines what. The work starts with policy. Authentication isn’t sufficient by itself to. authentication is a technique used to verify that someone is who they claim to be. This is usually done by. in its simplest form, access control involves identifying a user based on their credentials and then authorizing the appropriate level. It involves verifying the identity of the user or system requesting access. Authentication verifies the identity of the user,. authentication is the first step in access control. authentication and authorization are two vital information security processes that administrators use to protect systems and.
From docslib.org
Authorization and Access Control DocsLib What Is Authorization And Access Control authentication and authorization are two vital information security processes that administrators use to protect systems and. The work starts with policy. It involves verifying the identity of the user or system requesting access. This is usually done by. access control enforces both authentication and authorization policies to regulate access. authorization is the process of matching users to. What Is Authorization And Access Control.
From www.g2.com
Access Control Technology Glossary Definitions G2 What Is Authorization And Access Control authentication is a technique used to verify that someone is who they claim to be. Authentication isn’t sufficient by itself to. in its simplest form, access control involves identifying a user based on their credentials and then authorizing the appropriate level. authentication is the process of verifying someone’s claimed identity, while authorization determines what. It involves verifying. What Is Authorization And Access Control.
From www.vrogue.co
What Is Authorization And Access Control vrogue.co What Is Authorization And Access Control authorization is the process of matching users to the right digital assets. authentication is a technique used to verify that someone is who they claim to be. authentication is the first step in access control. The work starts with policy. access control enforces both authentication and authorization policies to regulate access. Authentication isn’t sufficient by itself. What Is Authorization And Access Control.
From olefins.com.bd
authenticationsystemforaccesscontrol Olefins Trade Corporation What Is Authorization And Access Control Authentication isn’t sufficient by itself to. This is usually done by. It involves verifying the identity of the user or system requesting access. authentication is a technique used to verify that someone is who they claim to be. authentication is the first step in access control. in its simplest form, access control involves identifying a user based. What Is Authorization And Access Control.
From www.geeksforgeeks.org
What is AAA (Authentication, Authorization, and Accounting What Is Authorization And Access Control access control enforces both authentication and authorization policies to regulate access. The work starts with policy. authentication is the process of verifying someone’s claimed identity, while authorization determines what. in its simplest form, access control involves identifying a user based on their credentials and then authorizing the appropriate level. This is usually done by. authentication is. What Is Authorization And Access Control.
From flamlabelthema.netlify.app
Role Based Access Control Matrix Template What Is Authorization And Access Control It involves verifying the identity of the user or system requesting access. authentication and authorization are two vital information security processes that administrators use to protect systems and. authorization is the process of matching users to the right digital assets. authentication is the process of verifying someone’s claimed identity, while authorization determines what. authentication is a. What Is Authorization And Access Control.
From braxtongrant.com
Understanding Key Identity & Access Management Components Blog What Is Authorization And Access Control Authentication verifies the identity of the user,. Authentication isn’t sufficient by itself to. This is usually done by. access control enforces both authentication and authorization policies to regulate access. in its simplest form, access control involves identifying a user based on their credentials and then authorizing the appropriate level. authentication is the first step in access control.. What Is Authorization And Access Control.
From www.vrogue.co
What Is Authorization And Access Control vrogue.co What Is Authorization And Access Control Authentication isn’t sufficient by itself to. authentication is a technique used to verify that someone is who they claim to be. This is usually done by. in its simplest form, access control involves identifying a user based on their credentials and then authorizing the appropriate level. Authentication verifies the identity of the user,. access control enforces both. What Is Authorization And Access Control.
From www.cerbos.dev
Designing an Authorization Model for an Enterprise Cerbos What Is Authorization And Access Control It involves verifying the identity of the user or system requesting access. This is usually done by. Authentication verifies the identity of the user,. authorization is the process of matching users to the right digital assets. authentication is the first step in access control. authentication is the process of verifying someone’s claimed identity, while authorization determines what.. What Is Authorization And Access Control.
From www.okta.com
What Is Authorization? Comparison with Access Control Okta What Is Authorization And Access Control authentication and authorization are two vital information security processes that administrators use to protect systems and. It involves verifying the identity of the user or system requesting access. This is usually done by. Authentication verifies the identity of the user,. authentication is the process of verifying someone’s claimed identity, while authorization determines what. authorization is the process. What Is Authorization And Access Control.
From cyral.com
What is Data Access Control? Definition and Related FAQs Cyral What Is Authorization And Access Control The work starts with policy. access control enforces both authentication and authorization policies to regulate access. authentication is a technique used to verify that someone is who they claim to be. It involves verifying the identity of the user or system requesting access. Authentication isn’t sufficient by itself to. authentication is the process of verifying someone’s claimed. What Is Authorization And Access Control.
From www.okta.com
Authentication vs. Authorization Okta What Is Authorization And Access Control This is usually done by. Authentication verifies the identity of the user,. authentication is a technique used to verify that someone is who they claim to be. in its simplest form, access control involves identifying a user based on their credentials and then authorizing the appropriate level. authentication and authorization are two vital information security processes that. What Is Authorization And Access Control.
From www.shieldoo.io
Authentication vs. Authorization Their Differences, Factors What Is Authorization And Access Control authentication is the first step in access control. authorization is the process of matching users to the right digital assets. This is usually done by. Authentication verifies the identity of the user,. authentication is the process of verifying someone’s claimed identity, while authorization determines what. authentication is a technique used to verify that someone is who. What Is Authorization And Access Control.
From support.tulip.co
Authorization and Access control using SAML What Is Authorization And Access Control authentication is the process of verifying someone’s claimed identity, while authorization determines what. authentication and authorization are two vital information security processes that administrators use to protect systems and. in its simplest form, access control involves identifying a user based on their credentials and then authorizing the appropriate level. The work starts with policy. Authentication verifies the. What Is Authorization And Access Control.
From study-ccna.com
What is AAA? Authentication, Authorization & Accounting Study CCNA What Is Authorization And Access Control access control enforces both authentication and authorization policies to regulate access. authorization is the process of matching users to the right digital assets. in its simplest form, access control involves identifying a user based on their credentials and then authorizing the appropriate level. This is usually done by. authentication is the first step in access control.. What Is Authorization And Access Control.
From fr.slideshare.net
Access Controls• Authentication & Authorization What Is Authorization And Access Control This is usually done by. It involves verifying the identity of the user or system requesting access. authentication is the first step in access control. Authentication verifies the identity of the user,. The work starts with policy. authentication is a technique used to verify that someone is who they claim to be. authentication and authorization are two. What Is Authorization And Access Control.
From cyberhoot.com
Access Control Mechanism CyberHoot What Is Authorization And Access Control authorization is the process of matching users to the right digital assets. access control enforces both authentication and authorization policies to regulate access. It involves verifying the identity of the user or system requesting access. authentication is the first step in access control. authentication is a technique used to verify that someone is who they claim. What Is Authorization And Access Control.
From www.f5.com
What Is Access Control? F5 Labs What Is Authorization And Access Control Authentication verifies the identity of the user,. authentication is a technique used to verify that someone is who they claim to be. The work starts with policy. It involves verifying the identity of the user or system requesting access. authentication is the first step in access control. authentication and authorization are two vital information security processes that. What Is Authorization And Access Control.